
Granular Policy Control and In-depth End-point Visibility
ExtremeControl extends the functionality within ExtremeCloud IQ – Site Engine. From a single screen, it enables the enforcement of consistent, highly secure access policies and the granular control of users and IoT devices for network onboarding. It helps protect corporate data by proactively preventing unauthorized users and compromised endpoints from gaining access to the network.
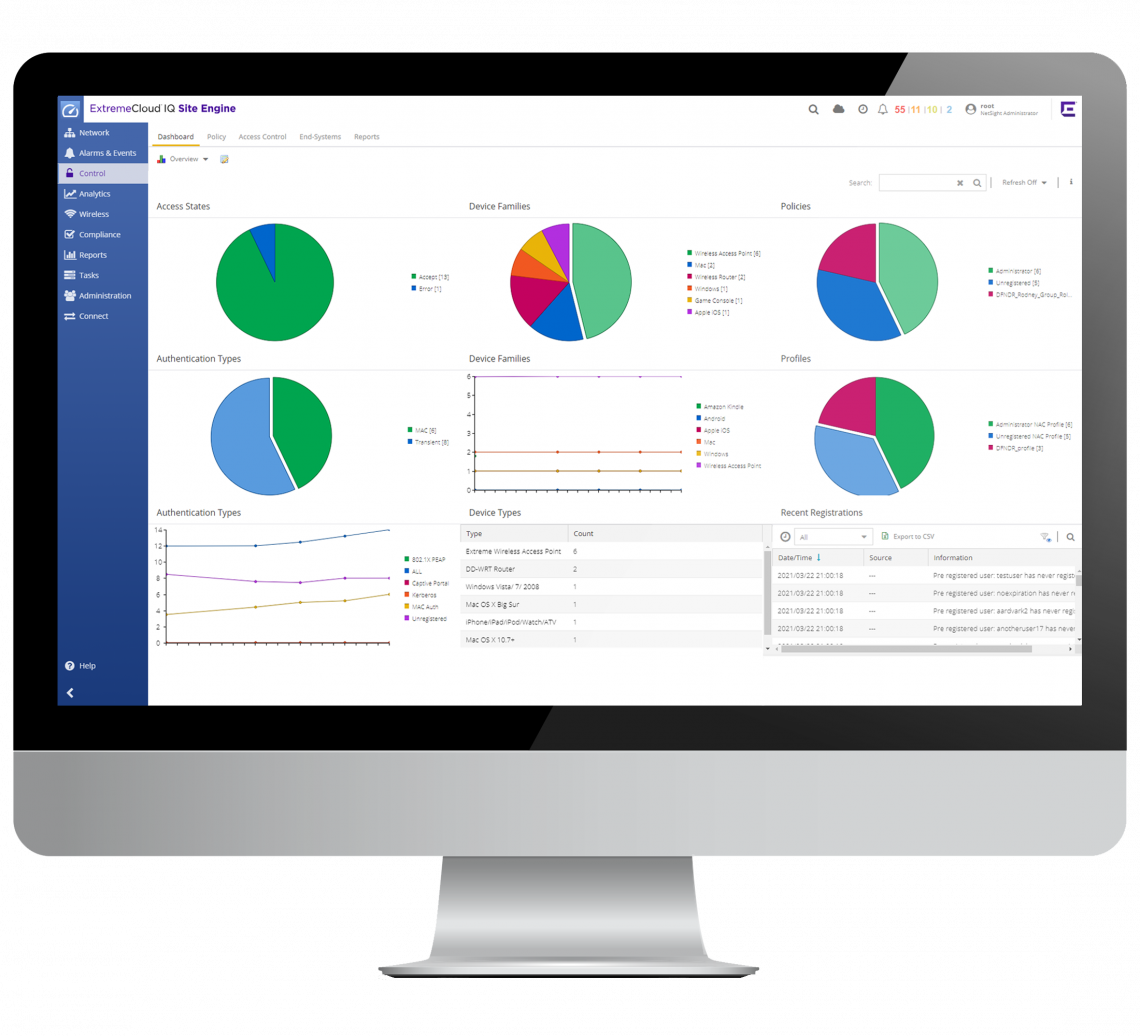
Enable secure BYOD, guest access and loT by rolling out real-time policies based on the security posture of devices.
Identify threats by profiling and tracking users and devices, as well as monitoring the health and compliance of devices before and after access.
Benefit from an array of integrated solutions via Extreme Networks’ ecosystem of partners to expand network security and threat response.